Linux Malware (Scenario 2)
The Linux Malware scenario uses the same infrastructure as the videoserver-scenario:
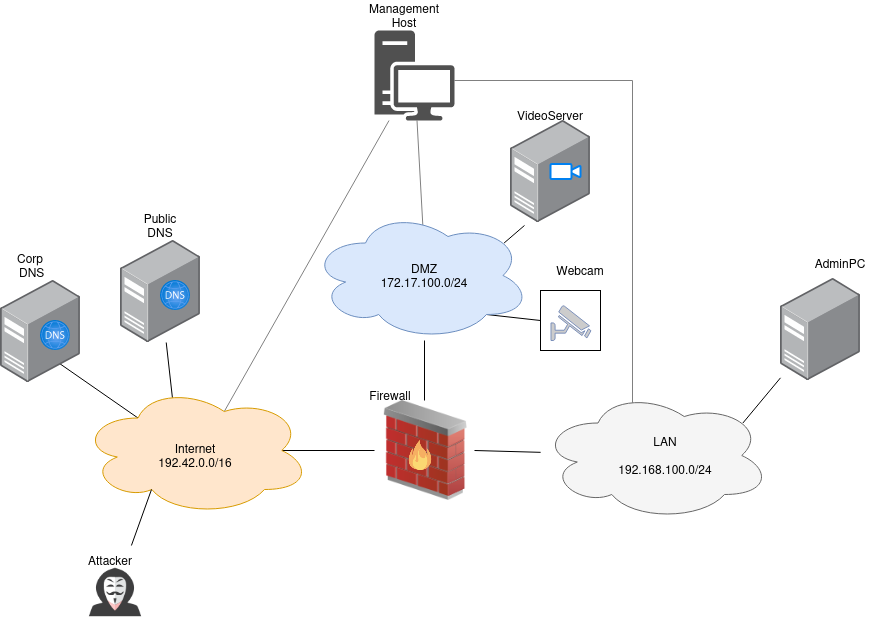
Attacker Steps:
Malware is installed and persisted:
sliver is installed via systemd(T1569, T1547, T1037)
sliver is executed via cronjob(T1053)
Malware executes commands (T1106, T1622, T1140)
Malware exfiltrates data(/etc/shadow) (T1071,T1132,T1001,T1573,T1572, T1041, T1048, T1030, T1020)
Malware uses a tar-archiv(T1560, T1074,T1005)
Malware discovers password policy(T1201)
Malware uploads nmap(T1105)
Malware executes nmap (T1046, T1018)
Attacker installs LD_PRELOAD Rootkit(T1014, T1564, T1574)
Attacker uses rootkit to gain root-privileges (T1574)
Attacker hides process via rootkit(T1014)
Hidden rootuser runs find against suid files(T1083)
Hidden rootuser discovers group-files(T1069)
Hidden rootuser runs nmap(T1046, T1018)
Hidden rootuser discovers password policy(T1201)