Lateral Movement (Scenario 3)
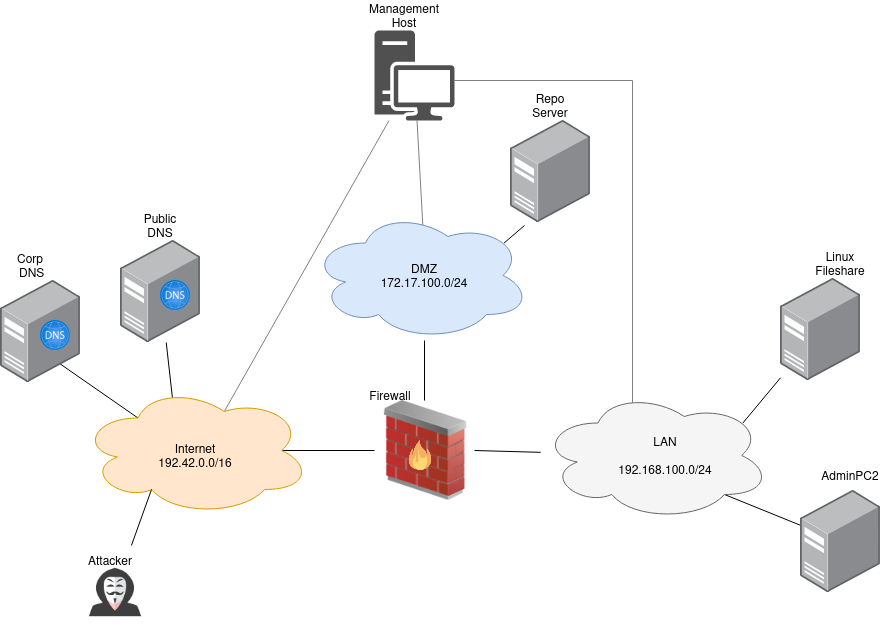
Attacker Steps:
Attacker brute-forces (T1078, T1133, T1110):
ssh
vnc
Attacker sniffs for credentials (server automatically logs into ftp) (T1040)
Pivilege Escalation via password reuse from point 3(T1078)
Attacker dumps password from /etc/shadow(T1003) which can be reused on other server
Attacker reads data from puppet-repository(T1213)
Attacker reads out information from other server network share(T1039)
Attacker runs nmap, ping, nmb-scan against other server(T1018, 1046)
Lateral Movement via
share: attacker replaces installation file that is used by another server(T1080)
exploit: attacker exploits a vulnerable service on another server(T1210)
apt: attacker replaces debian repository files which gets installed by another server(T1072)
puppet: attacker deploys backdoor via puppet(T1072)
On other host: (T1499)
remove account(T1531)
delete data (T1485 from share-folder)
encrypt data using ransomware(T1486, T1565)
Delete Backupfiles(T1490)
Stop Service(T1489)