Client (Scenario 6)
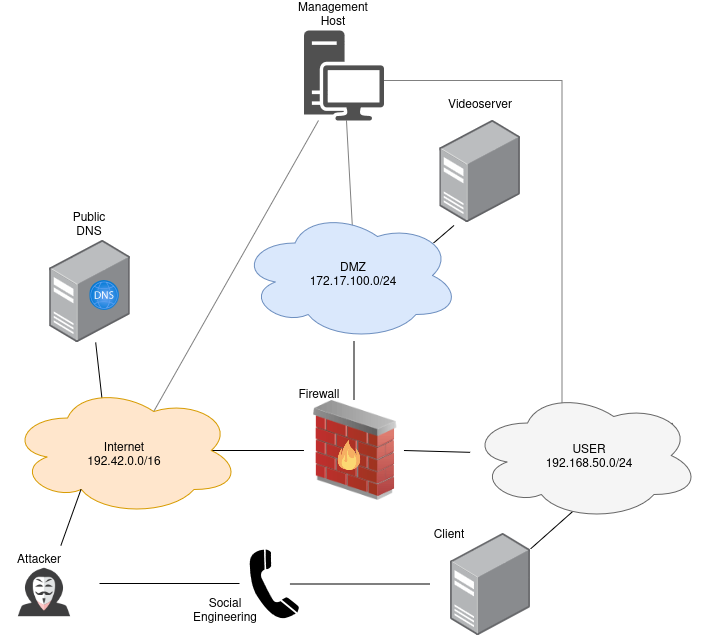
Attacker Steps:
Client gets exploited
Opening Open Office Document with malicious Macro (T1204)
Installing screen sharing software (T1219)
Attacker persists using icmp-malware(T1095)
by swapping binary of browser in $HOME(T1554)(T1546)
by installing cronjob as user(T1053)
Alternatively:
Client gets exploited
Installs malicious browser plugin (T1176)(T1203)
Plugin sends keystrokes to attacker (T1056.001)
Plugin sends formdata to attacker (T1056.004)
Plugin sends clipboard data to attacker (T1115)