Videoserver(Scenario1)
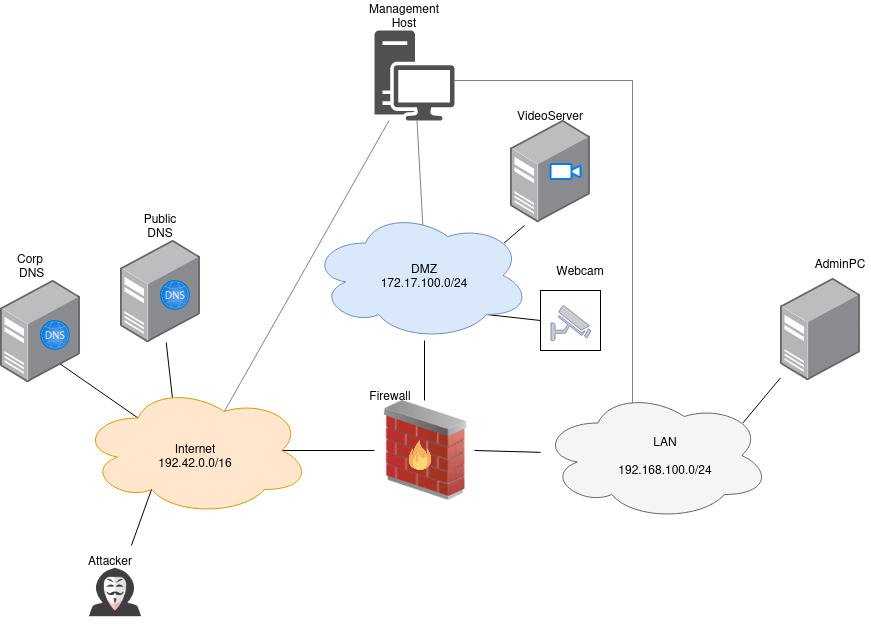
Attacker Steps:
Attacker scans DNS-Server of company with dns-brute(T1590,T1591)
Attacker scans Host with nmap(T1595) auch mit -O (T1592)
Attacker scans Host with nikto(T1595)
Attacker uses gobuster to crawl webserver(T1594)
Attacker penetrates zoneminder(T1190, T1059)
Attacker creates a stable reverse-shell(T1574, T1104) and attaches it to a running process(T1055 https://github.com/W3ndige/linux-process-injection) [KEIN PROZESS ATTACH]
Attacker uploads linpeas(T1105) and executes it(T1087, T1083, T1201, T1069, T1057, T1518, T1082, T1614, T1016, T1049, T1033, T1007, T1615)
Attacker finds privilege escalation
Polkit exploit(T1068, T1546, T1574)
Sudo weakness (T1548)
Misconfigured systemd-unit(T1547)
Logrotten(T1546)
Misconfigured cron-job(T1053)
Finds ssh-key for root-user(T1078)
Attacker gains root
Attacker adds backdoor
Attacker adds new ssh-key to authorized_keys(T1098)
Attacker creates new account(T1136)
Attacker modifies pam(T1556)
Attacker uses split to proxy command(T1218)
Attacker reads from /etc/shadow(T1555)
Attacker runs nmap(T1046) [VERSCHIEBEN IN ANDERES SZENARIO]
Attacker runs lspci and lsusb(T1120) [lsusb ist nicht installiert]
Attacker runs ntpdate or date(T1124) [ntpdate ist nicht installiert]
Attacker checks virtualbox-files(T1497)